Enhancing Intrusion Detection Capabilities in IoT Technologies through Machine Learning
IoT technologies connect physical objects via sensors and software. This technology allows automation, remote monitoring, and data-driven insights. You are going to see its use in sectors like healthcare, manufacturing, and smart cities.
Remote patient monitoring (RPM), Hospital Asset Management, Supply Chain Optimization, Quality Control, and Public Safety Systems are few examples of IoT technology use among many. RPM and smart medical devices utilize IoT remote monitoring technology for personalized treatments.
| Automation | Remote Monitoring | Data-driven Insights |
| Smart Home Systems | Remote Patient Monitoring | Predictive Maintenance |
| Industrial Automation | Environmental Monitoring | Supply Chain Optimization |
| Smart Agriculture | Asset Tracking | Energy Management |
| Autonomous Vehicles | Wildlife Tracking | Retail Analytics |
| Robotic Process Automation | Infrastructure Monitoring | Smart City Planning |
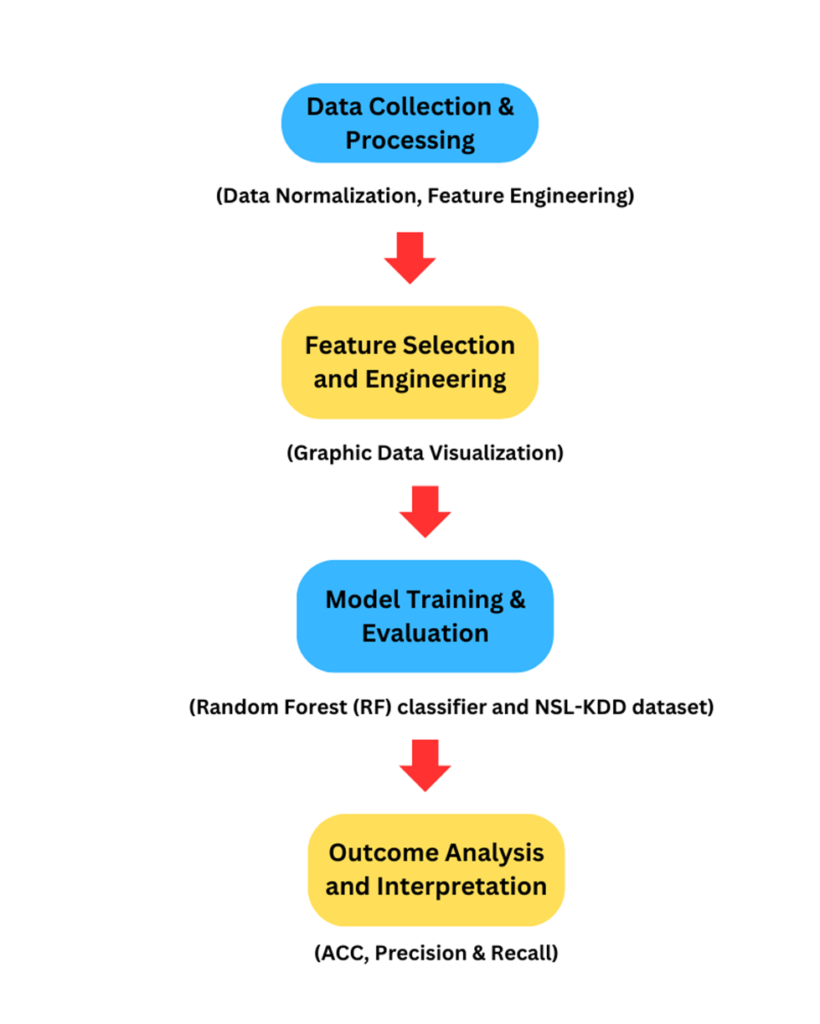
Using a dummy function to convert protocol_type was part of the feature engineering process. When the duration was more than 1500, anomalies were found. Additionally, the class_anomaly was set to 0 if the dst_bytes exceeded 50,000.
After graphic visualization, RF models were developed for class_anomaly. Shafiq et al identified top variables for DT, NB, RF, and SVM. In our proposed model for intrusion detection, we assessed the State_number and Stddev features.
· Srv_count: Number of services
· State_number: Numerical state representation
· Stddev: Aggregated record variation
What Are The Results?
In our research, We looked into the use of classification models to find IoT technology invasions. Predicting if an object belongs to the attack class using labeled data was one of the fundamental problems in intrusion detection. Predicted probabilities in binary classification can be interpreted in accordance with the outcome, which is either 0 or 1.
One important technique that has arisen for performance evaluation is the confusion matrix. It is useful to compare model predictions with real classes. This matrix aids in the computation of measures such as precision, recall, and accuracy (ACC). These metrics use Random Forest (RF) to assess intrusion detection systems (IDS).
ACC Calculation Equation:
ACC = tp+tntp+tn+fp+fn x 100%
r performance evaluation is the confusion matrix. It is useful to compare model predictions with real classes. This matrix aids in the computation of measures such as precision, recall, and accuracy (ACC). These metrics use Random Forest (RF) to assess intrusion detection systems (IDS).
The performance of the ACC model was greatly impacted by its use in our initial intrusion detection system. Finding the features that produce the best classification results allowed for the improvement of the RF classification model.
Two variables, src_bytes and dst_bytes, were used to evaluate the model after it was trained on the NS-KDD dataset. To further validate the chosen variables,For several parameters, we used the metric correlation values.
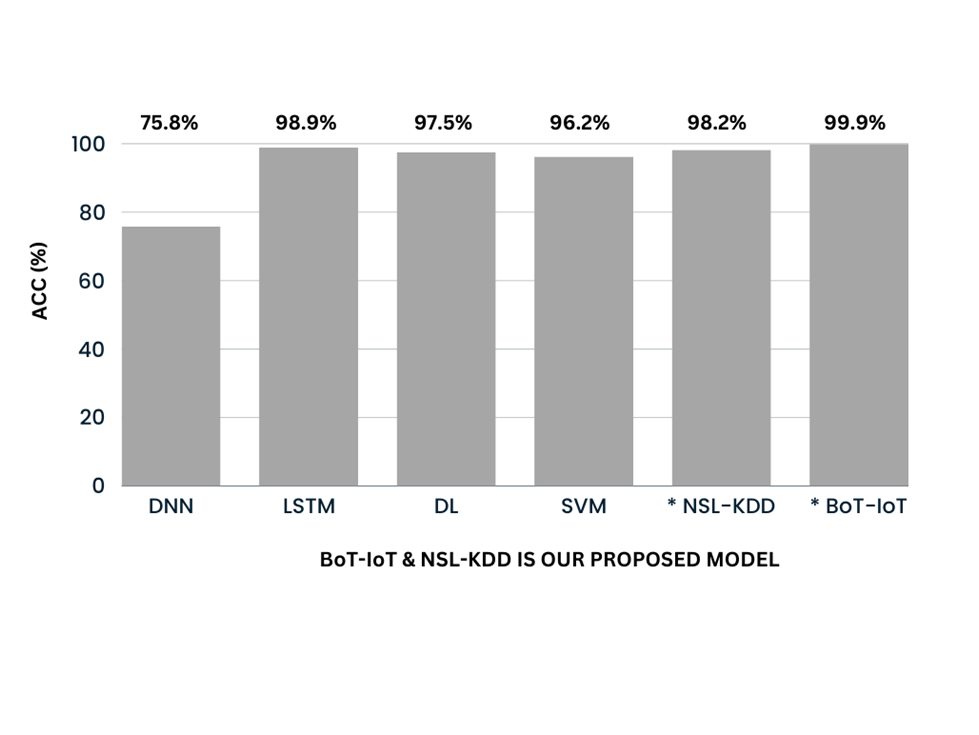
Using the BoT-IoT dataset, we additionally evaluated the model’s performance. To do this, we examined properties such as state_number and stddev. The picture illustrates the findings, which demonstrate how our suggested intrusion detection method outperformed alternative models in terms of ACC. Our approach also reduces the time needed for data collection and execution.
The RF classifier demonstrated the ability to distinguish between normal and aberrant traffic effectively. Our results indicate that RF outperformed other models such as Deep Neural Networks (DNN), Long Short-Term Memory (LSTM), Deep Learning (DL), and Support Vector Machines (SVM).
Summary
The speed of proliferation of Internet of Things (IoT) technologies has revolutionized domains like smart homes, industrial automation, healthcare systems and others. However, the widespread adoption comes with the inherent security challenges.
IoT devices are susceptible to various forms of cyber threats. Machine learning techniques for intrusion detection in IoT environments present a promising avenue for improving security measures.
This paper introduces a novel set of solutions aimed at mitigating security risks in IoT ecosystems. Specifically, it explores the use of Intrusion Detection Systems (IDS) coupled with Random Forest (RF) classifiers to identify and thwart malicious activities.
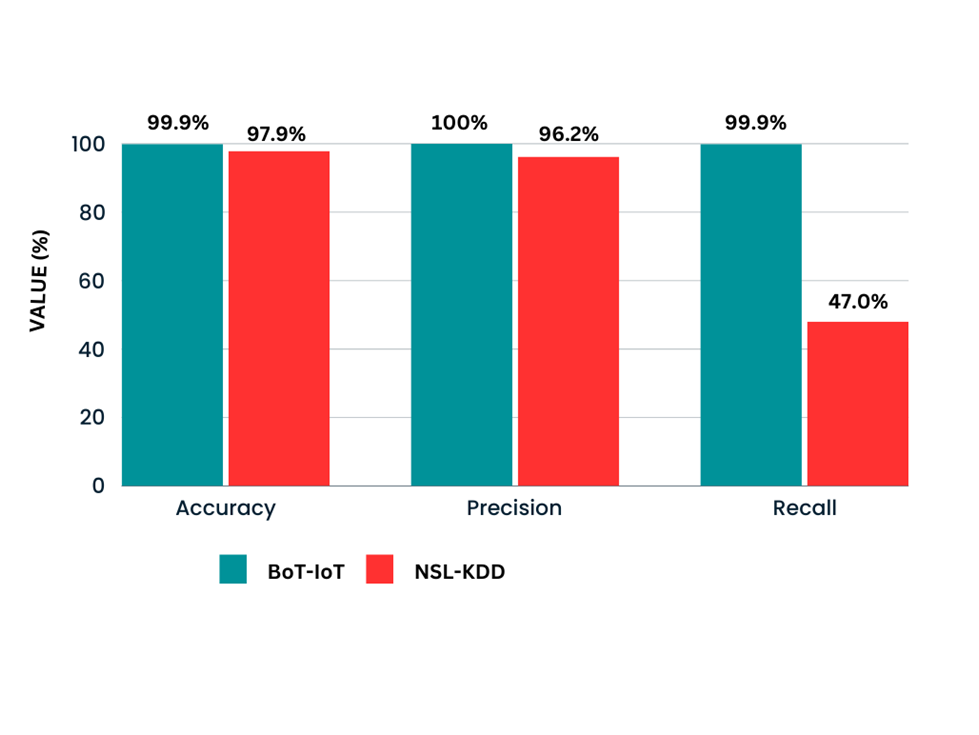
The proposed approach shows remarkable performance and it is proven by the results from two datasets: NSL-KDD (98.2% accuracy) and BoT-IoT (99.9% accuracy). Moreover, it demonstrates superior metrics in terms of accuracy (ACC), precision, and recall compared to existing methodologies.
Conclusion
Our research finding shows how useful it is to use machine learning for detecting intrusions in IoT technologies. We have shown ML algorithms like Random Forest can develop a more secure IoT network.
Datasets like NSL-KDD and BoT-IoT are used thoroughly to evaluate our work. Our study can be planned to be applied at different IoT situations, such as smart homes, healthcare, and industrial automation.
Starting the use of ML in intrusion detection systems means a more practical approach to stop threats before they happen. It is a big change for the security of IoT technologies. In the near future, study of more complicated models like Deep Learning and Real-time Monitoring will pave the road to make IoT security even better. So, our research does help to make IoT environments safer and digital ecosystems more resilient.
